DLP is a system designed to detect a potential data leakage incident in a timely manner and prevent it. When this happens, sensitive data such as personal/company information, credit card details, social security numbers, etc., is disclosed to unauthorized users either with malicious intent or by mistake. This has always been an important matter for most companies as the loss of sensitive data can be very damaging for a business.
To prevent or monitor the data leakage, exchange administrators had to rely on some 3rd party applications. But now Microsoft introduced a feature called DLP with Exchange server 2013 to achieve this.
How DLP Works
DLP works through DLP Policies, packages that contain a set of conditions made up of rules, actions and exceptions. These packages are based on Transport Rules and can be created in the Exchange Administration Center [EAC] or through the Exchange Management Shell [EMS]. Once created and activated, they will start analyzing and filtering e-mails. A nice feature is that you can create a DLP Policy without activating it, allowing you to test its behavior without affecting mail flow.
DLP Policies are nothing more than special Transport Rules. Because the transport rules with Exchange 2010 didn’t provide the means to properly analyze e-mail content, new types of transport rules were created in Exchange 2013 to make DLP possible. These allow information inside e-mails to be checked and classified as sensitive (or non-sensitive) based on keywords, dictionaries or even regular expressions, thus determining if an e-mail violates any organizational DLP Policies.
Another nice feature of DLP is called Policy Tips. These tips, similar to the MailTips introduced in Exchange 2010, inform senders that they might be violating a DLP Policy before they actually send the message! As we will see in the second part of this article, these Policy Tips only work on Outlook 2013 for now but it is just a matter of time until they appear in Outlook Web App as well.
DLP Operation Modes
Enforce Policy: the policy is enabled and all actions specified in the policy will be carried out
Test Policy with Notifications: the policy is enabled but the actions will not be executed, just logged into Message Tracking Logs. Policy Tips are displayed to users
Test Policy without Notifications: similar as above but no Policy Tips are displayed to users
There are three ways to create DLP policy
1. Through MS provided templates
The quickest way to start using DLP policies is to create and implement a new policy using a template. This saves you the effort of building a new set of rules from nothing. You will need to know what type of data you want to check for or which compliance regulation you are attempting to address.
2. Import a pre-built policy file from outside your organization
You can import policies that have already been created outside of your messaging environment by independent software vendors. In this way you can extend the DLP solutions to suit your business requirements
3. Create a custom policy without any pre-existing conditions. Your enterprise may have its own requirements for monitoring certain types of data known to exist within a messaging system. You can create a custom policy entirely on your own in order to start checking and acting upon your own unique message data. You will need to know the requirements and constraints of the environment in which the DLP policy will be enforced in order to create such a custom policy.
General Notes
1. After creating DLP polcies from defined templates, we can create a new rule to override the policy. For Eg: "Let’s add a new rule to automatically override the policy if the e-mail comes from the CEO."
2. We have to specify one "DLP Incident Mailbox" while creating rule. This mailbox will receive notification about each actions performed by DLP policies.
3. While creating custom DLP policy we can add sensitive information types (Passport numbers, Driving Licence numbers etc) and thresholds to take action.
Document Fingerprinting is a Data Loss Prevention (DLP) feature that converts a standard form into a sensitive information type, which you can use to define transport rules and DLP policies. For example, you can create a document fingerprint based on a blank patent template and then create a DLP policy that detects and blocks all outgoing patent templates with sensitive content filled in.
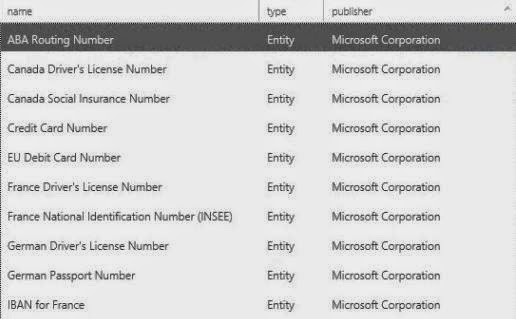
Sample sensitive information types
4. Thresholds
Minimum count: sets the lowest number of incidents at which the rule will be triggered. For example, if you set this field to 5 and the algorithm only detects 3 passport numbers in a message, the rule will do nothing;
Maximum count: sets the highest number of incidents at which the rule will be triggered;
Minimum confidence level: sets the lowest confidence level at which the rule will be triggered. Similar to a Spam Confidence Level, the algorithm used is obviously not 100% accurate so this field allows us to tweak the detection “certainty” if necessary;
Maximum confidence level: sets the maximum confidence level at which the rule will be triggered.
5. Policy Tips
6. Message Tracking Log for the blocked email also the sender will receive an NDR.





Bruegmann Group Loss Prevention is the concept of establishing policies, procedures and business practice to prevent the loss of inventory or monies in a retail environment. Developing a program around this concept will help you to reduce the opportunities that these losses can occur and more specifically, work to prevent the loss rather than solely be reactive to them after they occur.
ReplyDelete